[Security: Entra ID] The World Of Risky Users & Agents In EntraID

In this blogpost we're going to talk about Risky Users & Agents in Microsoft Entra ID. What are Risky Users, how does MS classifies these risks detections, what are the requirements and how do I configure this? Also we take a little step further and reviewing the new Risky Agents tab and user remediation that are currently in Preview.
1. What Are Risky Users And How Does Microsoft Knows/Collects This?
Risky users are user accounts that are being investigated by Microsoft and then flagged as possible compromised. Events like unfamiliar locations (impossible travel), unfamiliar sign-ins or failed login attempts but also events like leaked credentials or certain malicious patterns in a users sign-in (AiTM attack).
*Note: You will need to have a P2 license.
1.1 Data Collection
Now you may be wondering how this data is being collected. Microsoft daily analyses trillions of sign-in logs/signals from M365 customers and their users using machine learning. These are of course all anonymous. All this data can be used to identify and detect for example malicious IP's/locations, a malicious pattern (AiTM attack) or analyse this data for leaked credentials from the darkweb.
Beside above, Microsoft of course also collects data from your own company is order to know more about your situation. Data like where does this person mostly logon from, from where and with what type of device/browser. With this data collected a baseline will be created for each user so that it does understand when to give a risky user alert using machine learning.
2. Types Of Risks Levels
Within Risky Users we have three different level types: low, medium and high. Each level represents different risk criteria based on the machine learning described above. To be more precise I will give some examples per risk level:
Risk level Low:
A user with the risk level classified as Low typically exhibit standard behavior patterns. These users are most often performing secured activity from familiar locations and are not showing any signs of unusual behavior. Most of these users also have a clean history of security incidents or policy breaches.
Risk level Medium:
A user with the risk level classified as Medium displays more atypical behaviors and needs to be closer monitored. For example these users may login from various locations or from new devices. Also short login sessions can cause the risk level to set to medium. There are ofcourse more triggers but these are the most common.
Risk level High:
A user with the risk level classified as High have a significant unusual behavior indicating potential threats. Users with this classification often leads to immediate actions to make these accounts secure again. Some examples that can trigger a High risk are downloading large amounts of data, leaked credentials or impossible travel.*note: be aware that a user also can initiate a high risk by reporting themself a suspicious MFA prompt. Also you will need to configure CA policies to auto respond to a Risky user level. Per default Microsoft won't do anything if a Risky user is detected apart from sending you a notification (if configured).
3. Alerts & Notifications
The first thing you want to do is configure alerts, so when a risky user occurs you will get a notification.
The first thing we want to do is browse to the Entra Admin Center:
Go to the Entra admin center (entra.microsoft.com)
Browse to ID Protection -> Dashboard -> Under Settings, select "Users at risk detected alerts"
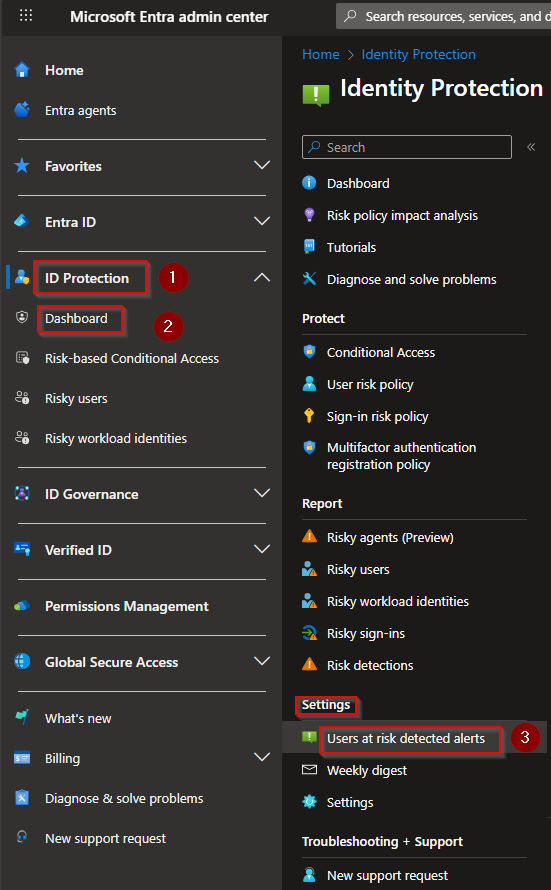
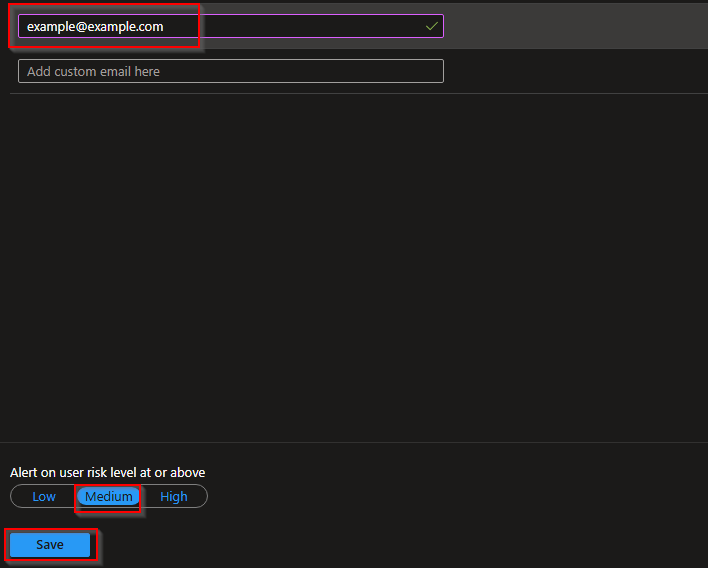
From this page you will be able to add a custom email address. I recommend setting notifications from risk level Medium or above:
Now when we have a Risky user that has a level Medium or above, we will receive an email looking like this:
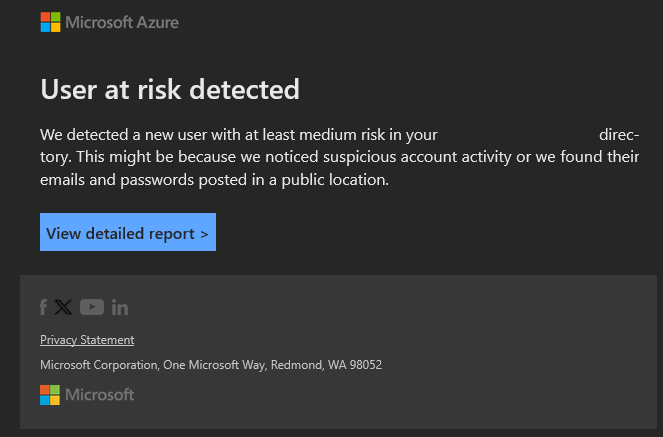
Now if we zoom in a little bit further and select "View Detailed Report", we will see a overview of the user that's having a Medium risk level. You can select the user you want to investigate. From this user page you can now select a couple of logs you want to see, for example "Risky Sign-In" or "Risk Detections". You could also take immediately action and for example block the user or revoke its sessions.
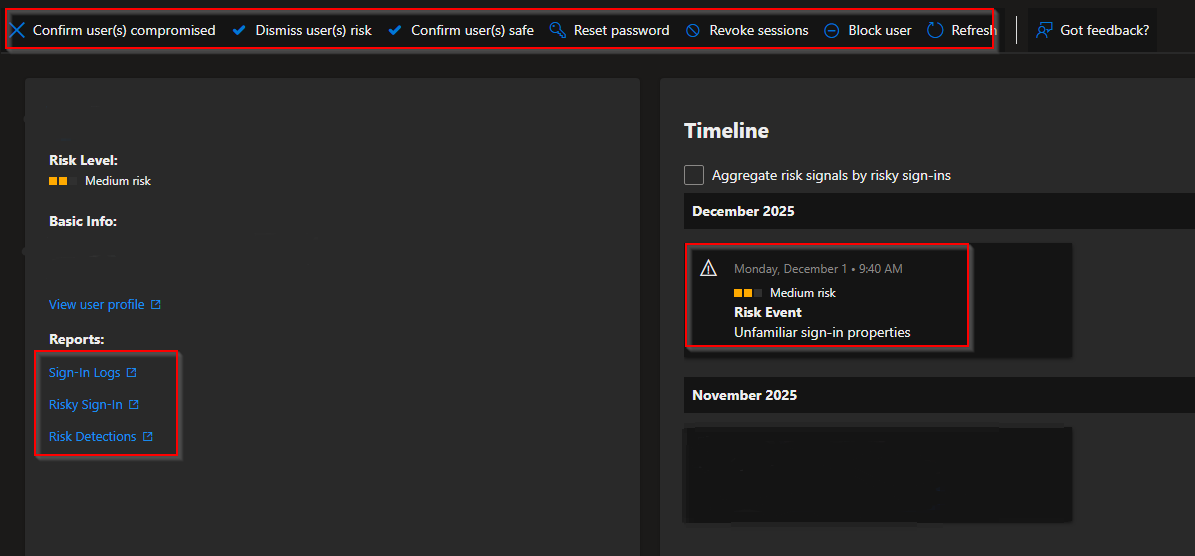
In the "Risk Detections" detail page we could see that this user has "Unfamiliar sign-in properties" and is trying to log in from Las Palmas:
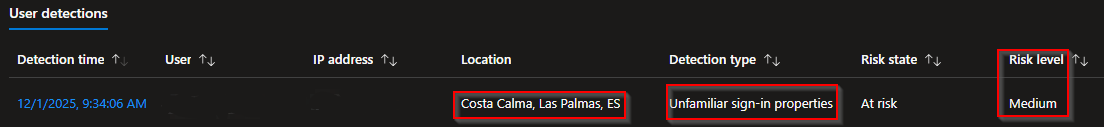
To see more details select "Detection time". Under "Additional Info" we will see more information regarding this sign-in:
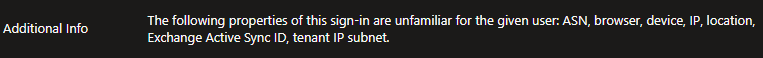
This user was allowed to login from a different location but because of the machine learning described in the previous chapter it was still giving a Medium risk level with the reason described the "Additional Info".
3.1 Higher Level Notifications
You could/should also setup more higher level notifications to get more alerts from your M365 environment using Microsoft XDR. Follow these steps to configure these notifications as well:
The first thing we want to do is browse to the Microsoft Defender:
Go to the Microsoft Defender (security.microsoft.com)
Browse to System -> Settings -> General -> Under General, select "Email notifications"
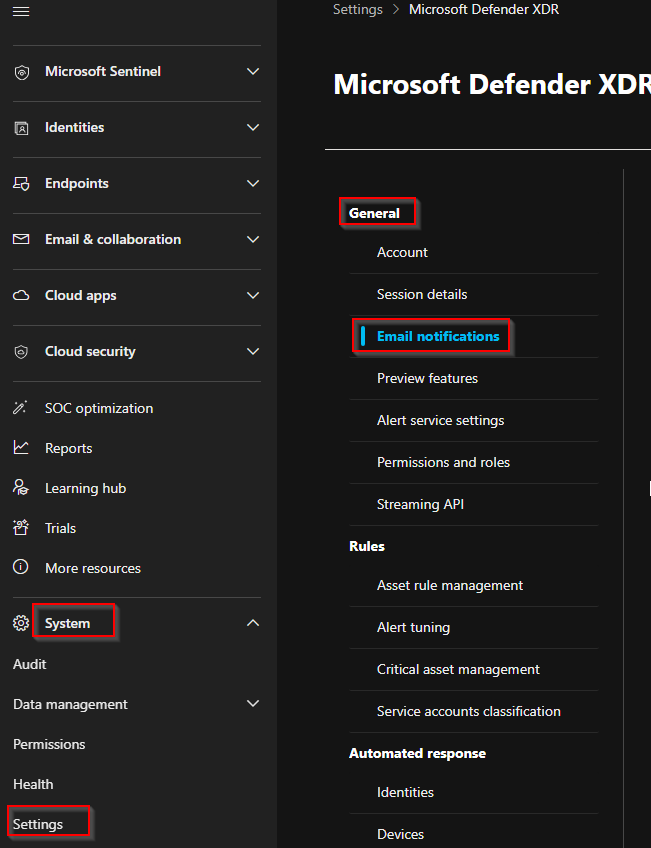
From the Email notifications screen select "Add incident notification rule":
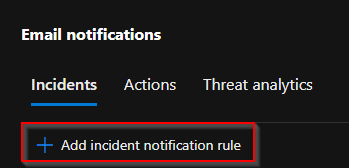
A new screen will appear. Give the policy a name and select Next. Next you will get the notification settings menu. Depending on your license I recommend selecting all the sources that you have a license for and selecting for example Low, Medium and High as "Alert Severity".
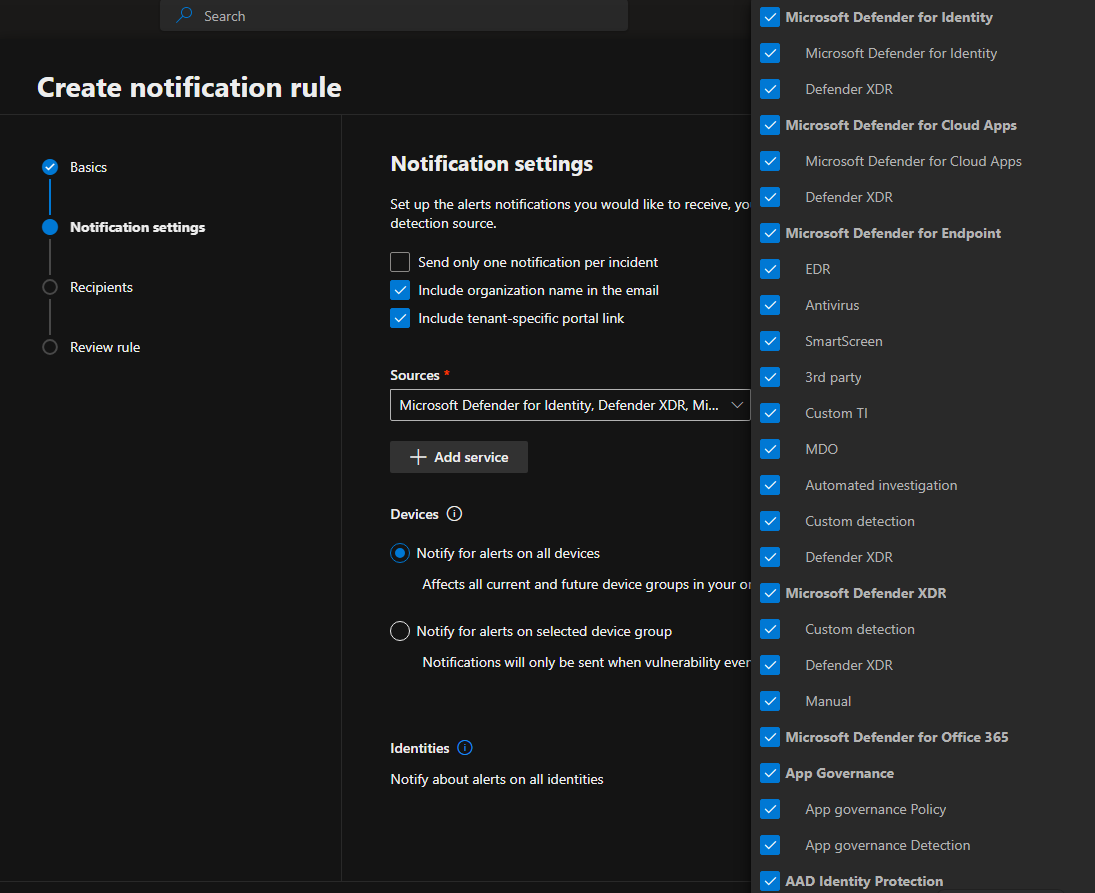
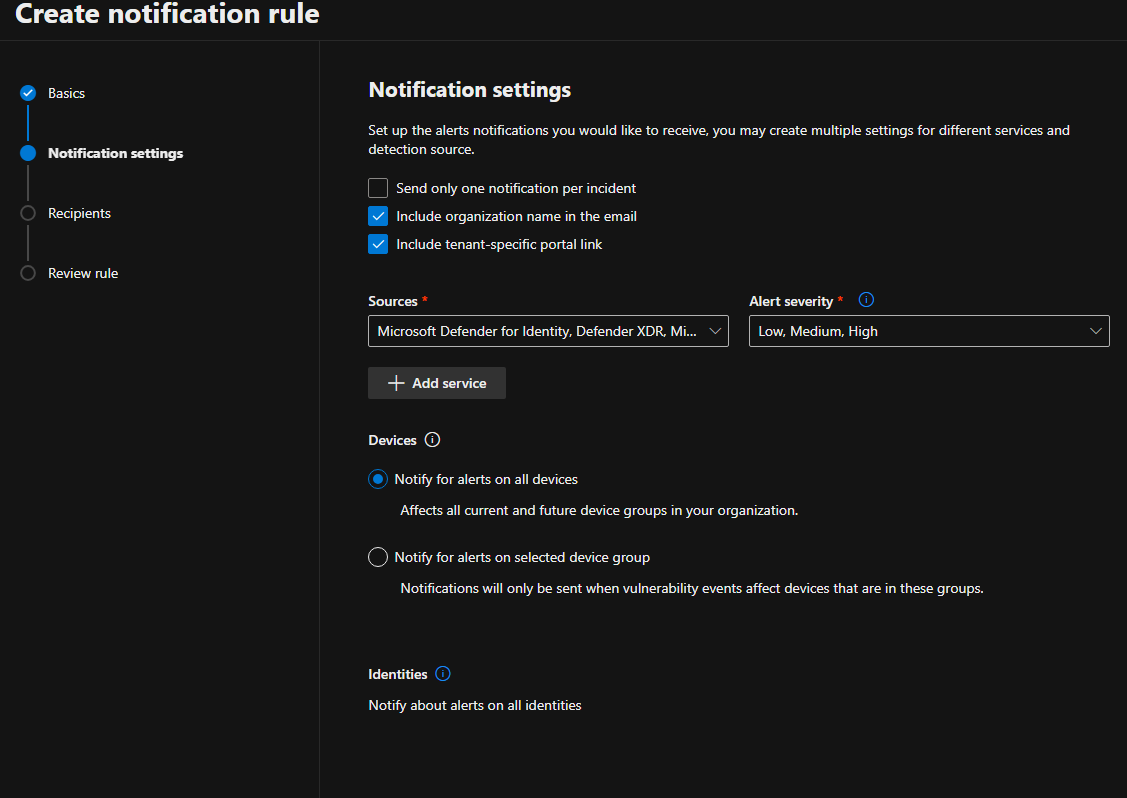
*Note: you are able to create different "Alert Severity" per source if you want. For example you only want to have Medium or High alert severity for Microsoft Defender for Endpoint.
Select Next. Now you will get the "Recipients" menu. From here enter the email address you want to sent the notifications to and select "Next". Now review your policy and select "Submit"
4. So What Now? (CA Policies)
What we want to do is ensure the potential breach or token theft from happening. There are some configurations we could create in order to stop the first attempt of attack. There are many options that we could configure, but I will discuss a few:
4.1 Block High Risk Sign-Ins / Block High User Risk
Follow these steps to make sure that a medium and high risk user (sign-in) will be automatically blocked from signing in. Because the steps are almost the same I will combine these two in this post but I strongly recommend creating two different CA policies:
*Note: You will need to have a Entra ID P2 or Entra Suite license.
The first thing we want to do is browse to the Entra Admin Center:
Go to the Entra admin center (entra.microsoft.com)
Browse to Entra ID -> Conditional Access -> select "Create new policy"
Give the policy a name and set these configurations:
Users or agents (Preview)
Include: Select "All Users"
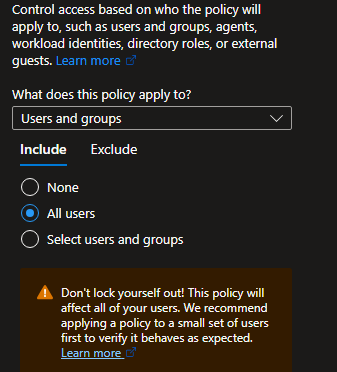
*Note: Don't lock yourself out. Configure if necessary breakglass access
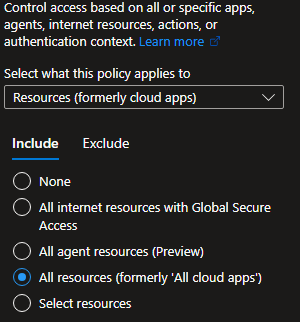
Target resources
All resources (formerly 'All cloud apps')
Conditions
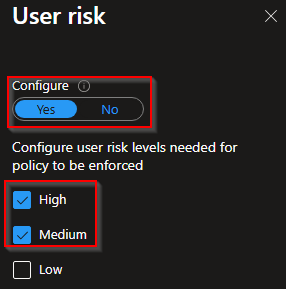
Sign-in risk: Configure -> Yes -> Medium, High
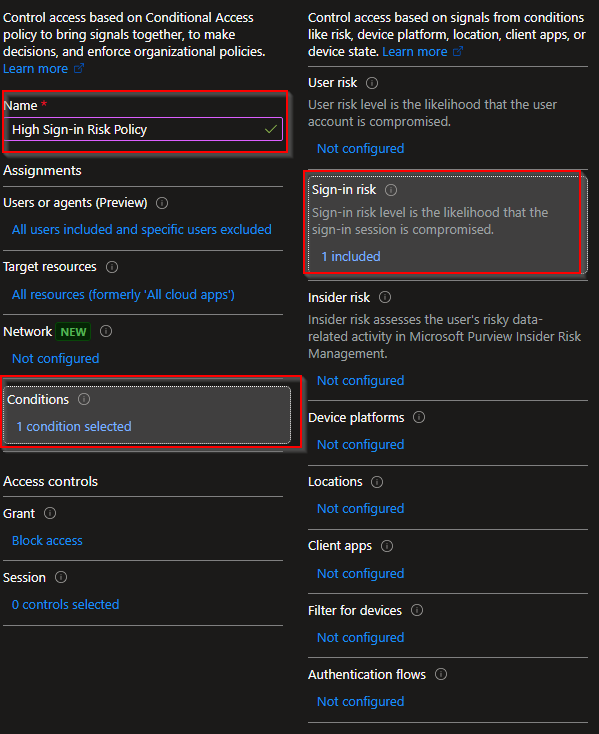
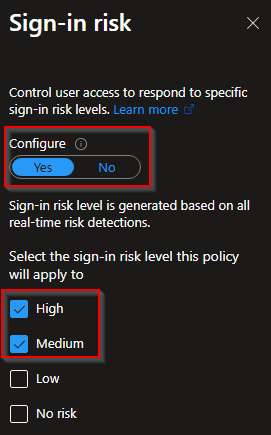
Conditions
User risk: Configure -> Yes -> Medium, High
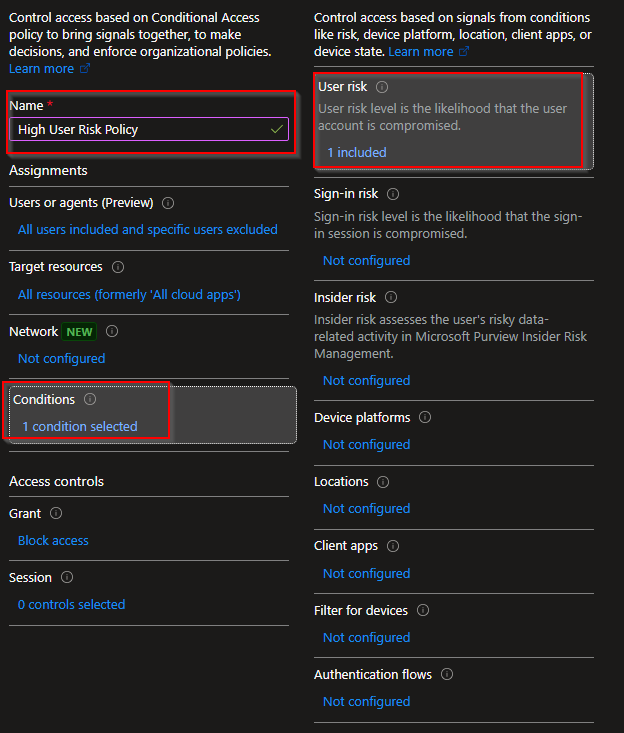
Access Controls
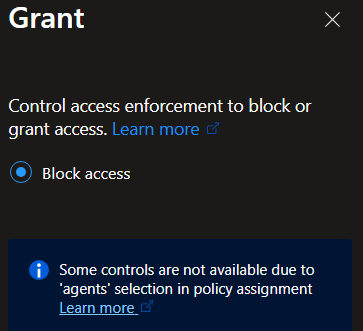
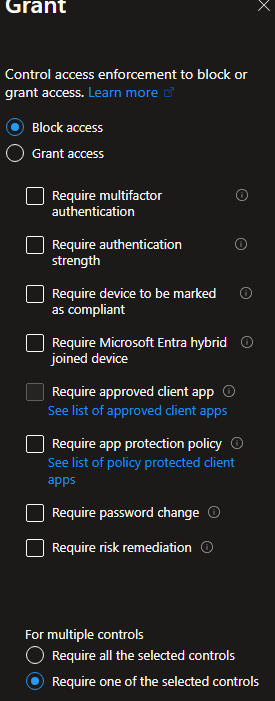
Select "Block Access"
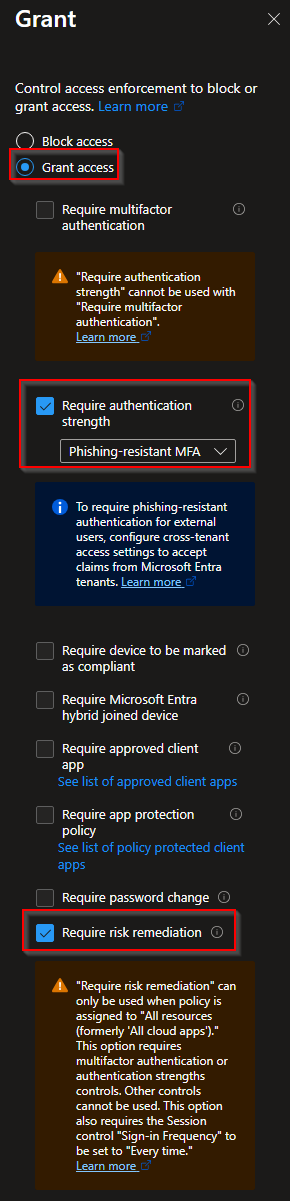
4.2 Require Risk Remediation (Preview)
Now Microsoft has introduced a new remediation option in Conditional Access. Because we are more and more moving over to passwordless we want to create something a user can do by themself. A high risk user remediation will be a password change but this gets more difficult if you are using a passwordless option already. With this remediation option users will be able to "reset" their risk level themselfs. This option works for both ways (users with password and passwordless)
Follow these steps to create this policy:
*Note: You will need to have a Entra ID P2 license and this will only work for risk remediation so not sign-in risks.
*Note2: Select which users/groups are using passwordless already in this policy as it can't be combined with the options I described above (Block). Also external and guest users must continue to self-remediate through secure password reset, as Microsoft Entra ID doesn't support session revocation for external and guest users.
The first thing we want to do is browse to the Entra Admin Center:
Go to the Entra admin center (entra.microsoft.com)
Browse to Entra ID -> Conditional Access -> select "Create new policy"
Give the policy a name and set these configurations:
Users or agents (Preview)
Include: Select "All Users" or Select your passwordless group/users

Target resources
All resources (formerly 'All cloud apps')

Conditions
Sign-in risk: Configure -> Yes -> High
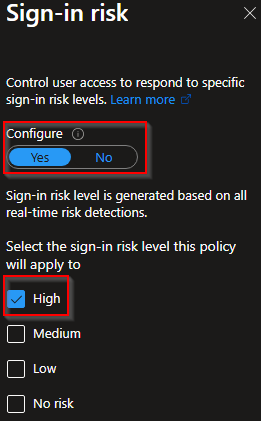
Access Controls
Select "Require risk remediation"
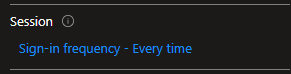
While selecting this option you will see that other options will also be activated (Require authentication strength) and that the Sign-in frequency will be set to Every time. It's being set to every time because all sessions will be revoked for that specific user.
To test this out we could set a (test)user to compromised using Powershell/Graph:
Import-Module Microsoft.Graph.Identity.SignIns$params = @{
userIds = @(
"29f270bb-4d23-4f68-8a57-dc73dc0d4caf"
"20f91ec9-d140-4d90-9cd9-f618587a1471"
)
}
5. Risky Agents
Now that we've talked about Risky users we have another player in town named Risky Agents. Agents will be part of our environment more and more. These agents can have a lot of access rights that can be risky. Microsoft now has the option to monitor these risky agents as well. In part 2 of this blog I will deep dive in the settings you could do and how to remediate/setup CA policies.
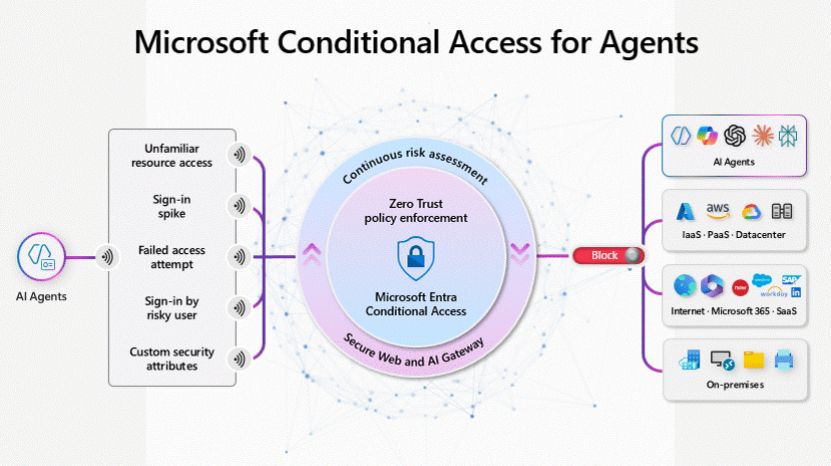
5.1 How does this work?
To trigger a Risky Agent alert, Microsoft is monitoring the following:
- Unfamiliar resource access - this means if a agent is connecting to sources it normally never does
- Sign-in spikes - this means if a agent is signing in many times
- Failed access attempts - this means if a agent is signing in multiple times to a resource it doesn't have access to
- Sign-in by a risky user - this means a agent can login as a user which already is risky
- Confirmed compromise - this means a agent is confirmed comprimised (after the admin acknowledged this)
- Threat intelligence signals - this means a monitored agent is aligned with the threat intelligence signals giving by Microsoft.
5.2 Great! Where can I see these Risky Agents?
You may be wondering where you can find these Risky Agents. To view these Agents you can browse to the same location as where we can find our Risky Users.
The first thing we want to do is browse to the Entra Admin Center:
Go to the Entra admin center (entra.microsoft.com)
Browse to ID Protection -> Dashboard -> Under Report, select "Risky agents (Preview)"
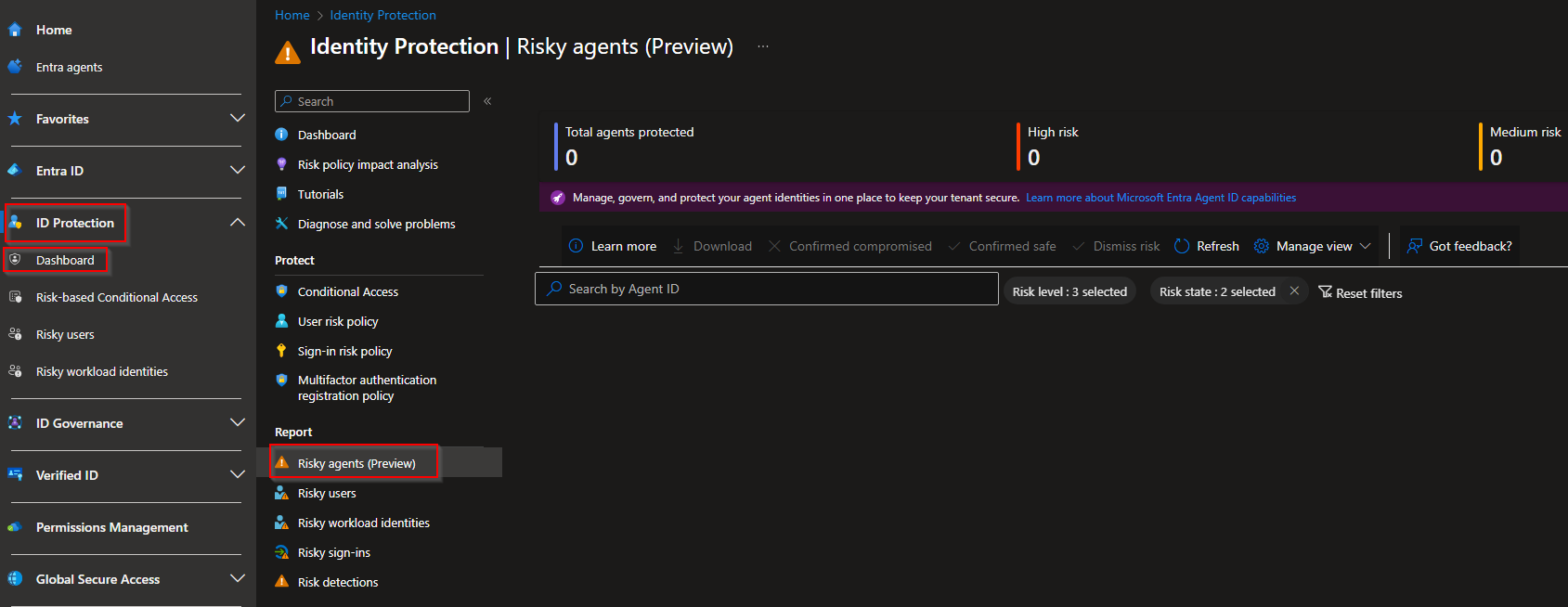
From this page we can see all our Risky Agents that we want/need to investigate. We can investigate/see different changes described above. For example changes to permissions or to see which sign in is being used for this Agent.
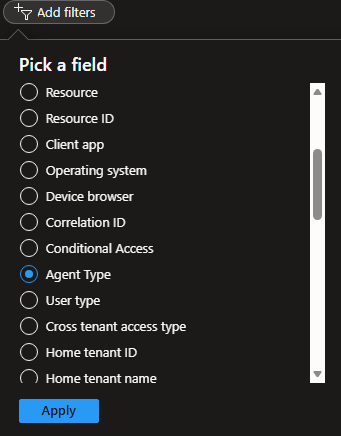
You can also see the agents in the Sign-ins logs by filtering agentType, agent user or agent identity. Beware that some events will be shown in the User sign-ins (non-interactive) while others appear under Service principal sign-ins.
- Agent identities (actor) accessing any resources -> Service principal sign-in logs -> agent type: agent ID user
- Agent users accessing any resources -> Non-interactive user sign-ins -> agentType: agent user
- Users accessing agents -> User sign-ins
source MS Learn
5.3 And How About Conditional Access Policies For Agents?
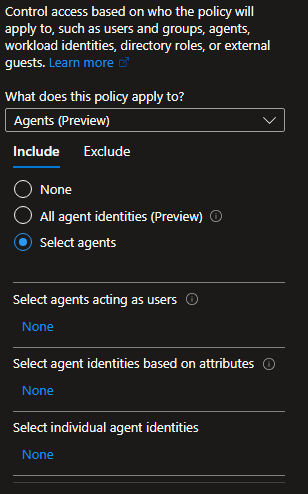
Microsoft also has options for creating CA policies for your (Risky) Agents which is currently in preview. There are some changes compared to the Risky Users CA policies. A Agent for example cannot initiate MFA. You can configure multiple options, for example block a High risk Agent or select agents acting as users. The following options can be configured:
- Select agents acting as users
- Select agent identities based on attributes - for example block all agents with the security label "test"
- Select individual agent identities - for example block all agent identities but allow the ones that are reviewed and approved.
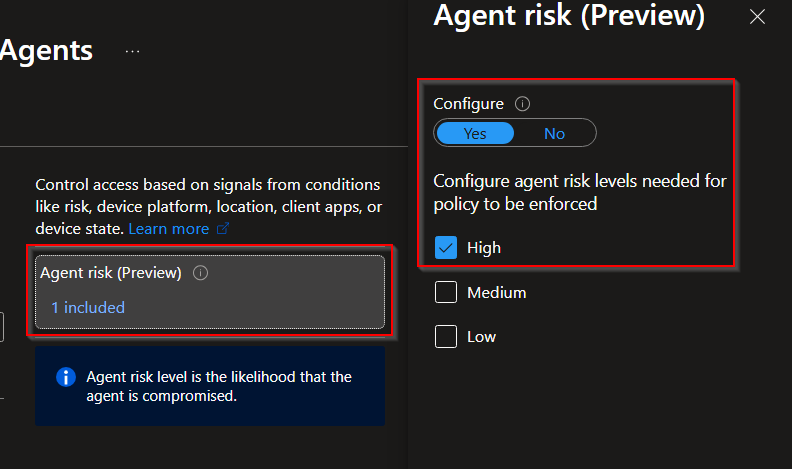
In this example we are going to block all agent identities with High level.
The first thing we want to do is browse to the Entra Admin Center:
Go to the Entra admin center (entra.microsoft.com)
Browse to Entra ID -> Conditional Access -> select "Create new policy"

Give the policy a name and set these configurations:
Users or agents (Preview)
Include: Select "Agents (Preview)" following "All agent identities (Preview)
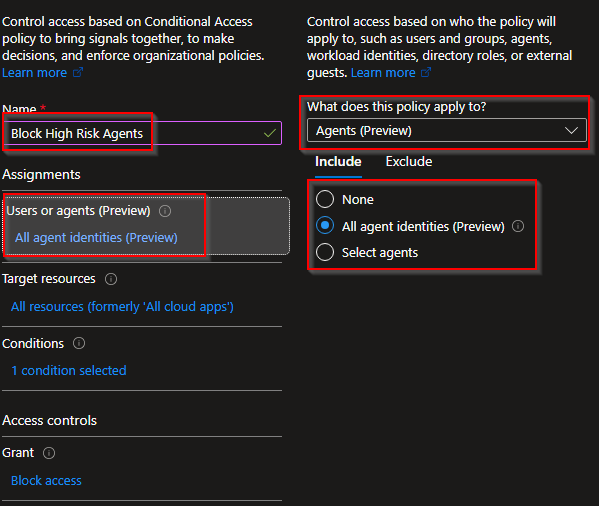
Target resources
All agent resources (Preview)

Conditions
Agent risk (Preview): Configure -> Yes -> High
Access Controls
Select "Block Access"