[Security: Entra ID] Secure Your Temporary Access Pass

In this blogpost we're going to talk about TAP (Temporary Access Pass) in Microsoft Entra ID. What is TAP, what are the requirements and how do I configure this?
1. What is Temporary Access Pass?
With temporary access pass (TAP) you can set a passcode for a limited time for a user. You can use this passcode for single use or multiple sign-ins.
TAP can be your go to when you want a new user to setup their passwordless autentication method the first time they login.
*Note: You will need a Entra ID P1 or P2 (if you want to use governance features like Access Packages) license.
2. Configure TAP Authentication Method
The first thing we want to do is browse to the Entra Admin Center:
- Go to the Entra admin center (entra.microsoft.com)
- Browse to Entra ID -> Authentication methods
From here we select "Temporary Access Pass".
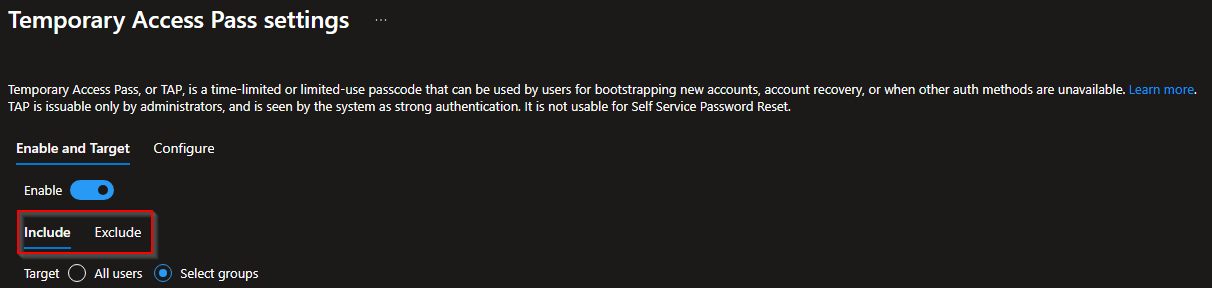
From the TAP settings menu we can configure several options like enabling and in-exclude users or groups. I recommend setting the include to selected groups instead of using all users. Setting this to all users will also include your privileged accounts which we don't want. If you don't want to set this to a group but still want to use all users be aware to still exclude your privileged accounts.
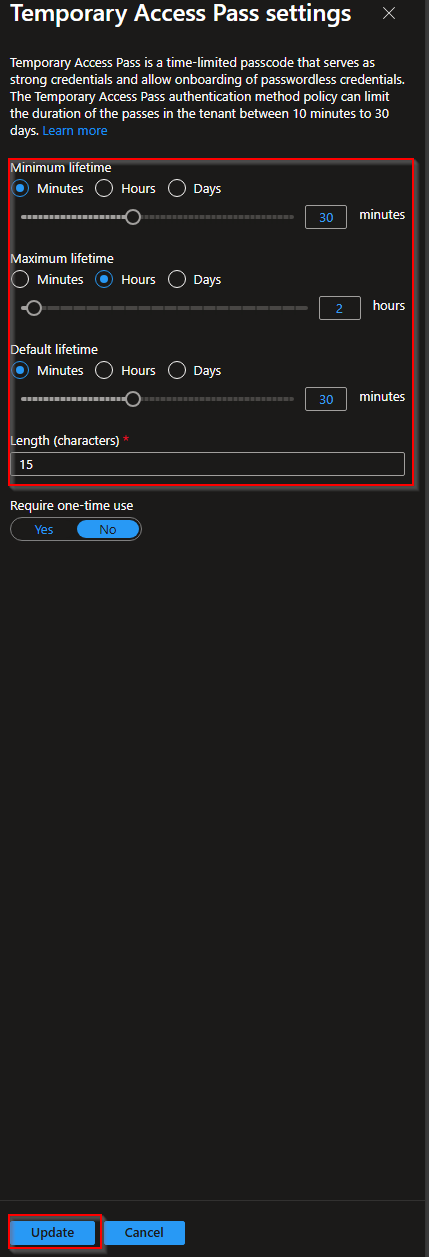
Next select "Configure".
From the configure menu select "Edit". In this options menu we can configure the length of activation time the TAP can be used. I recommend setting the following:
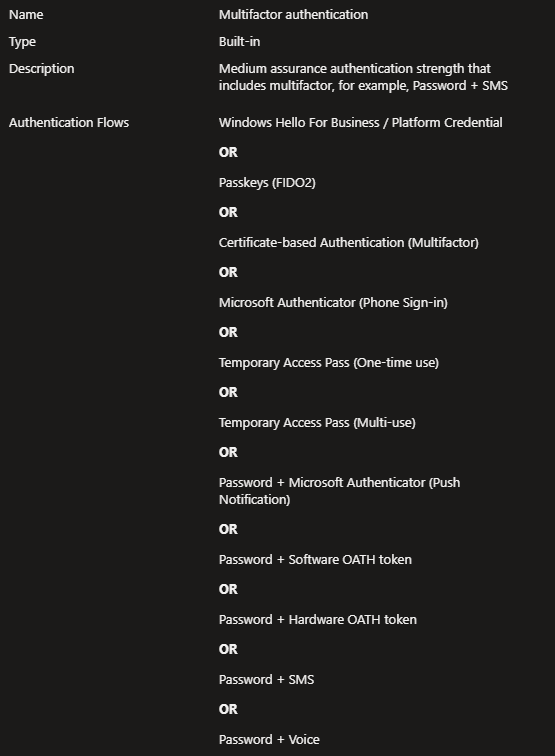
3. Authentication Strengths And TAP
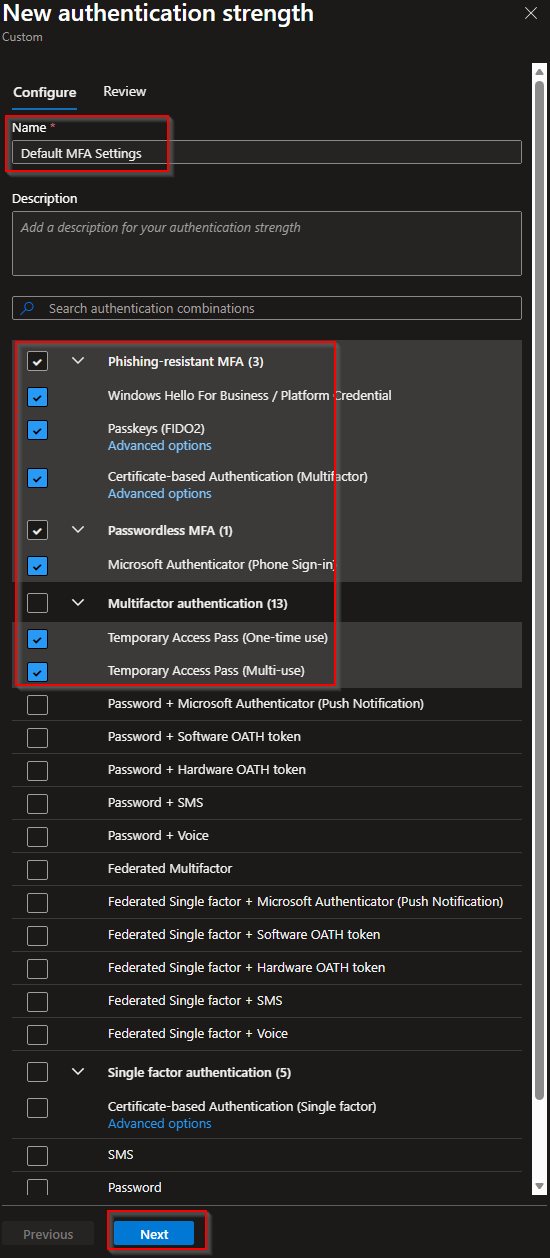
By default Microsoft creates three authentication strenghts in your environment (MFA, Passwordless MFA and Phishing-Resistant MFA). For the first one TAP is available as authentication method, but for Passwordless and Phishing-Resistant MFA, TAP isn't enabled by default. As we cannot change these default Authentication Strengths we want to create a new "clean" one.
The default MFA works great with TAP but it also has all options enabled (like SMS, Voice), which we don't want to use anymore right. Also if you are not using the default but have a custom build like we are going to configure, be aware to check if TAP is enabled in your custom Authentication Strength.
Because I like clean policies/auth methods I recommend creating a custom Authentication Strength where we will only configure those authentication flows that we want/are allowed to use.
Follow these steps to create a custom authentication strength:
Browse to authentication methods -> select "Authentication Strengths".
Select "New Authentication Strenght"
From the new auth strength screen select the following and select "Next":
*Note: These options are my preferred, but if you have an existing environment you might also select some more options in order to have a smooth migration to passkey and not locking yourself/organization out. See my other blog on how to identify which methods your organization is using.
Be sure to have a CA policy that's asociated with this new created authentication strenght and that your users(s) are included in this policy. You could use the CA template named "Securing security info registration" that's available from CA overview page.
Also be sure that your passkey authentication method includes your user(s) or group.
4. Test it out!
Now to see this in action we are going to configure a TAP for a specific user and see what it does!
The first thing we want to do is browse to "Users" in the Entra admin center.
Search and select the user you want to create a TAP for. Next browse to "Authentication Methods"
From here we want to select "Add authentication method"
Next select "Temporary Access Pass" as method and configure the one-time use and the duration.
*Note: You could choose to always set one-time use also in the configuration of the TAP auth method. Also be aware that TAP will bypass your MFA(if this is an existing user with MFA configured), so only configure the time needed to reregister MFA.

We now have a TAP for our user. You can now instruct your user to browse to https://aka.ms/mysecurityinfo where they can configure MFA. Using TAP can also be used when for example you want to rollout a Autopilot device for a specific user.
*Note: Copy the password because it will only be visible once. When you close the screen you will not be able to view the password again.
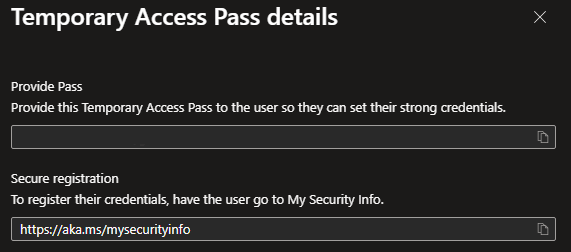
Now If we browse to the security info site you will see that it will ask for our TAP password.
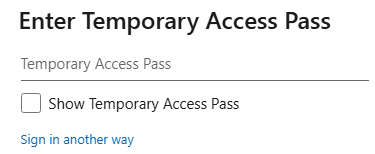
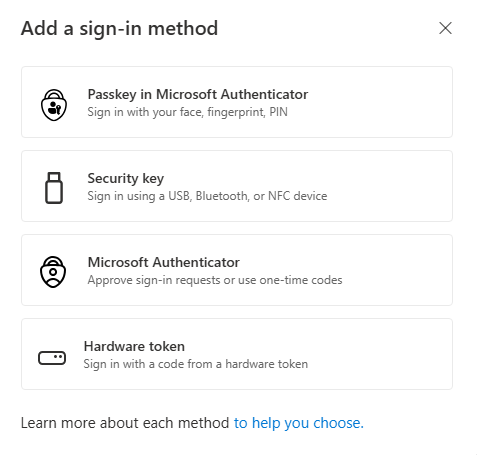
After we filled in our TAP we can configure (for example) a Passkey for this user account.
In the Sign-In logs we can also see that the TAP has been used.

You could also use Powershell to set a TAP:
Import-Module Microsoft.Graph.Identity.SignIns
$params = @{
startDateTime = [System.DateTime]::Parse("2025-01-01T00:00:00.000Z")
lifetimeInMinutes = 60
isUsableOnce = $false
}
New-MgUserAuthenticationTemporaryAccessPassMethod -UserId example@example.com -BodyParameter $params
5. Great, But Who Can Create/Set A TAP?
By default, the following Microsoft Entra ID administrator roles can configure or view a TAP for a specific user (source: MS Learn). The first two roles listed are the least-privileged options for managing TAP:
Privileged Authentication Administrators: create, delete, and view a TAP for admins and members, but never for their own account.
Authentication Administrators: create, delete, and view a TAP for members, but not for their own account.
Authentication Policy Administrators: enable or disable TAP, include or exclude groups, and fine-tune the Authentication Methods policy for TAP.
Global Readers: view TAP configuration details for a user, but cannot see the actual TAP code.