[Security: Entra ID] Passkey Profiles And Auto-Enable (March 2026)

In this blogpost we're going to talk about passkeys profiles that are going to be auto-enabled from March 2026. What is going to change and what is my recommendation regarding these profiles?
1. What is going to be auto-enabled?
From March 2026 Microsoft is auto enabling the use of Passkeys profiles in your tenant. With Passkey profiles you are able to configure a set of rules that you can use to targeted groups to ensure the registration and authentication with passkeys. With this change you will also be able to use synced Passkeys. With synced passkeys you can synchronise your key to other providers like Keeper, 1Password and many others. With these synced keys you will be able to choose from device bound or device bound and synced based on your enforce attestation.
1.1 So What If I Don't Do Anything?
If you don't opt-in via the Passkey authentication method configuration, you will be auto migrated to these profiles starting from March 2026. Keep in mind that your current configuration settings will be migrated into a default Passkey profile including user/group targeting that you have configured at this moment.
1.2 Registration Campaign
Be sure to check your registration campaign as this is also going to change some settings if you have this set to "Microsoft-Managed" and have set the passkey property to "synced".
Please keep in mind that the following will change if you have this configured as "Microsoft-Managed":
The "Authentication method" will change from "MS Authenticator" to "Passkeys"
Default user targeting will be updated from "voice call"/"text message" to "all MFA capable users"
"Limited number of snoozes" and "days allowed to snooze" cannot be configured anymore and these settings will be auto configured as "unlimited snoozes" with a "one day" reminder.
2. How Can I Check This?
The first thing we want to do is browse to the Entra Admin Center:
- Go to the Entra admin center (entra.microsoft.com)
- Browse to Entra ID -> Authentication methods
From the authentication methods we first want to check our "Registration campaign" settings:
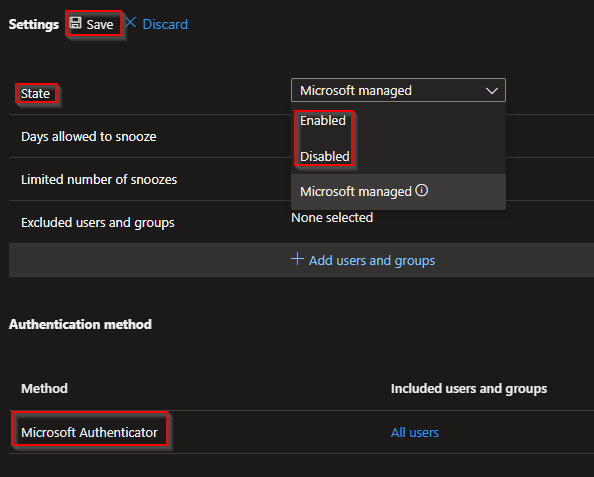
Here we can see our "state" and snooze settings as described above that will auto change when your "state" is configured as "Microsoft-managed". You can also see your "Authentication method" that now has been configured as "Microsoft Authenticator" and will change to "Passkeys" (if passkey type property is set to synced).
Now you have two options regarding settings the "state". If you don't want to change MS Authenticator to Passkey you want to set the "state" to "Enabled" or "Disabled".
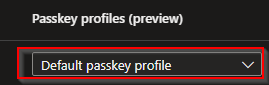
Next we move over to our "Policies" and select "Passkey (FIDO2)":
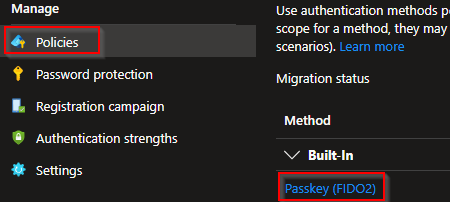
If you haven't opt-in to the public preview you might see a banner showing you the option to do so (this option will disappear from March 2026):
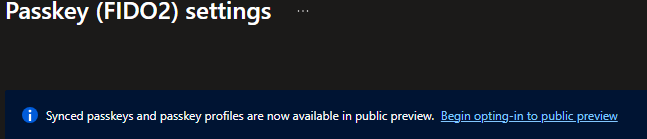
After you selected "begin opting-in to public preview" you will get a message to edit your default passkey profile:
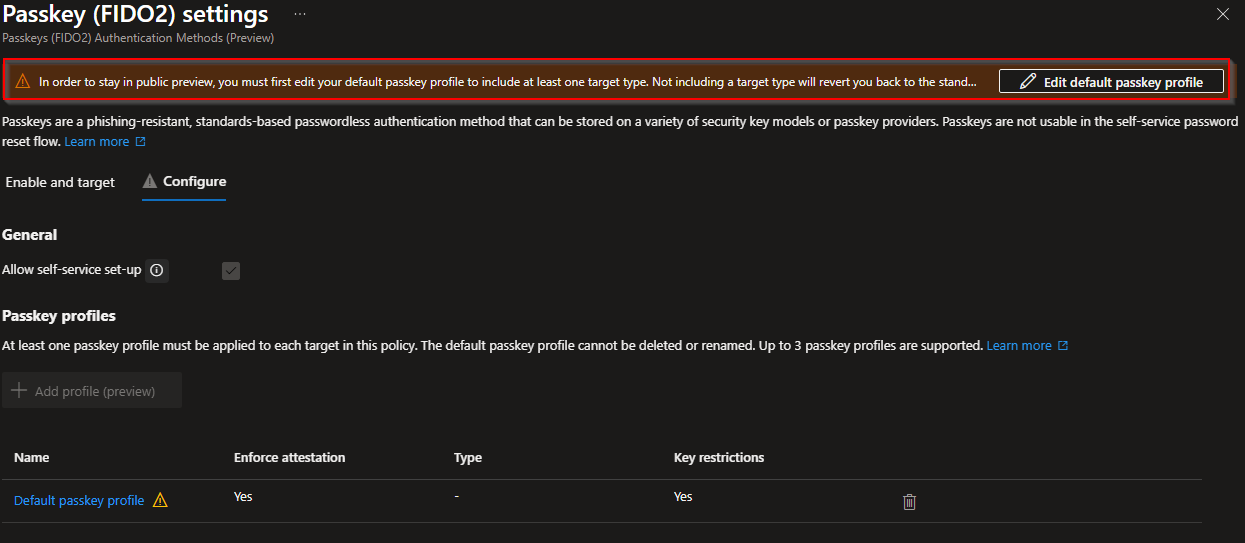
Select "Edit default passkey profile". A new Passkey profile screen will appear. Name your Passkey profile and select the configurations you want to have as default.
Depending if you want to sync your passkey, you should choose the options that's suits your security needs. For example you could set a default profile where "normal" accounts are allowed to be synced to a third party provider where another profile doesn't allow this (for example your admin account(s).
I don't recommend syncing your admin passkey to another provider.
To allow/disallow "synced passkeys":
- Enforce attestation
- if you enable this you will only have a "device-bound" key
- Disable enforce attestation
- if you do not select this option/leave is unchecked you could choose for "device-bound" and "synced"
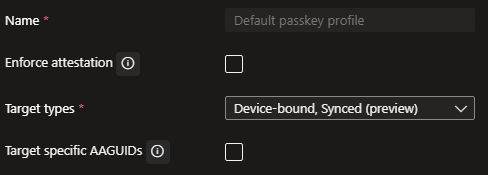
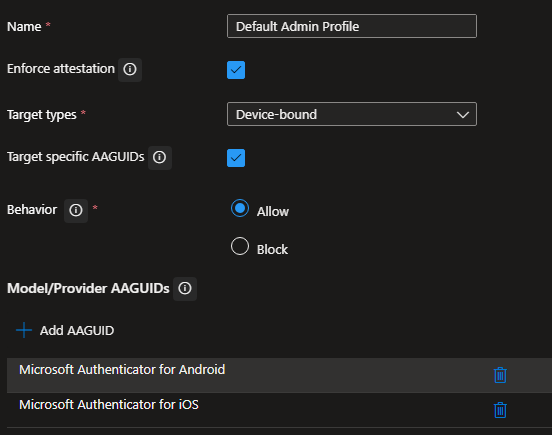
When you created these two configurations you will be able to target specific groups and configure which profile that specific group needs to use (default vs admin).