[Security: Entra ID] Extend Entra Sign-In Logs (Beyond 30 days)

In this blogpost we're going to talk about extending your Sign-In logs beyond the default 30 days (when using P1/P2 license).
By default, Microsoft Entra ID retains sign-in logs for only 30 days. I personally advise to extend this period. In order to extend this period we are going to configure and setup a Log Analytics Workspace. *note: You will need a subscription in order to configure this Workspace.
why longer retention matters:
- Security investigations: Threats often go unnoticed for weeks or months. Historical data is crucial for tracing incidents.
- Compliance requirements: Standards like ISO 27001 or NIS2 may require log retention of 90 days or more.
- Behavioral analysis: Understanding user trends over time helps improve security posture and detect anomalies.
Note that this option is most suitable for small organizations. If you work at a large organization I would recommend using Microsoft Sentinel as this is a robust SIEM and you have the ability to use advanced hunting.
1. Workspace Analytics
Now we are going to create a Log Analytics workspace in order to extend our logs. Logs that you can extend are:
- Sign-In Logs;
- Security Logs;
- Audit Logs;
- Custom Logs;
- Activity Logs.
By sending Entra sign-in logs to a workspace, you have the following options:
- Extended retention: Up to 730 days.
- Advanced querying: Use KQL to filter, correlate, and visualize data.
- Alerting: Set up custom alerts based on log patterns.
- Integration with Microsoft Sentinel: For full SIEM functionality.
2. Setting Up Analytics Workspace
We are now going to configure our workspace. Please keep in mind that you will need a active subscription:
Subscription
Go to the Azure portal and browse to "Subscriptions"
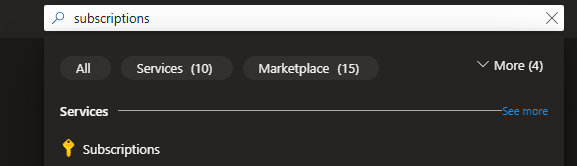
Next, select "Add" to add a subcription and select your offer. For this blog I will use "Pay as you go"
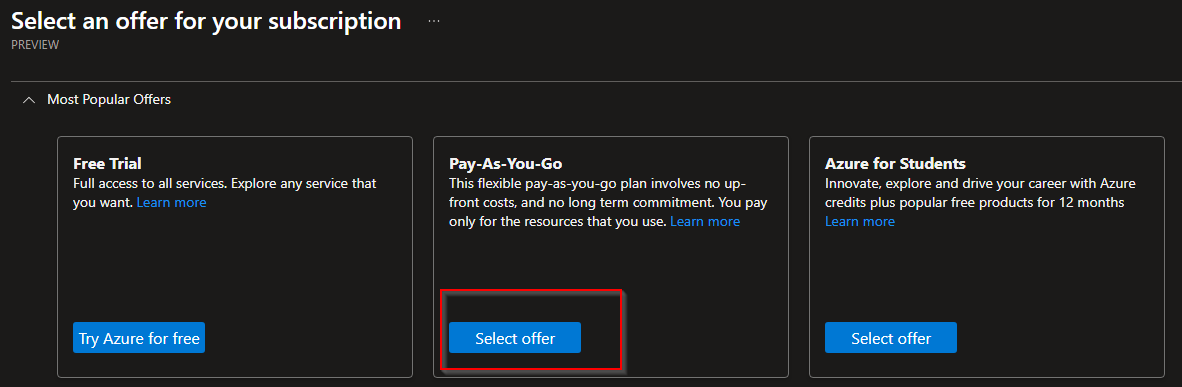
Follow the instructions on your screen to complete the setup. From here we are going to create a Log Analytics Workspace
From Azure browse to "Log Analytics Workspace"
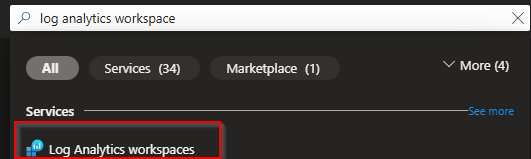
From the log analytics workspace page select "+ Create"
Fill the required information (Subscription, Resource Group, Name and Region) and select "Create"
*Note: make sure you select the correct AZ Region!
Now that we have created a new Log Analytics Workspace we are going to configure Entra ID
Browse to Entra ID (entra.microsoft.com)
From Entra ID navigate to "Monitoring - Diagnostic settings"
From the Diagnostic settings menu select "+ Add diagnostic setting"
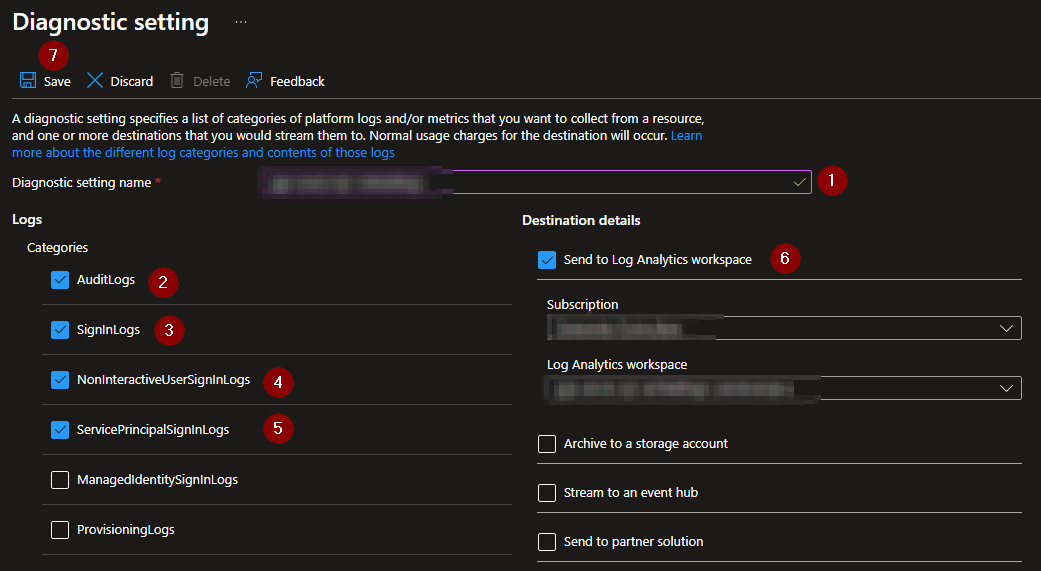
From the add diagnostic settings menu we can add the logs we want to sent to the workspace (for example sign-in logs, audit logs, ServicePrincipalSignInLogs). Select the logs you want to pass trough and select our just created Log Analytics Workspace. Next click "Save" and we're done!
Now that we have forwarded our logs to the Log Analytics Workspace we want to make sure we extend the default of 30 days. To configure this browse to our just created Log Analytics Workspace. From the workspace go to "Tables" and select the log you want to extend.
*Note: It can take a bit before you see your Logs in the Workspace
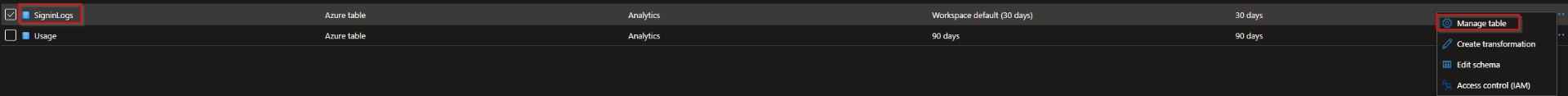
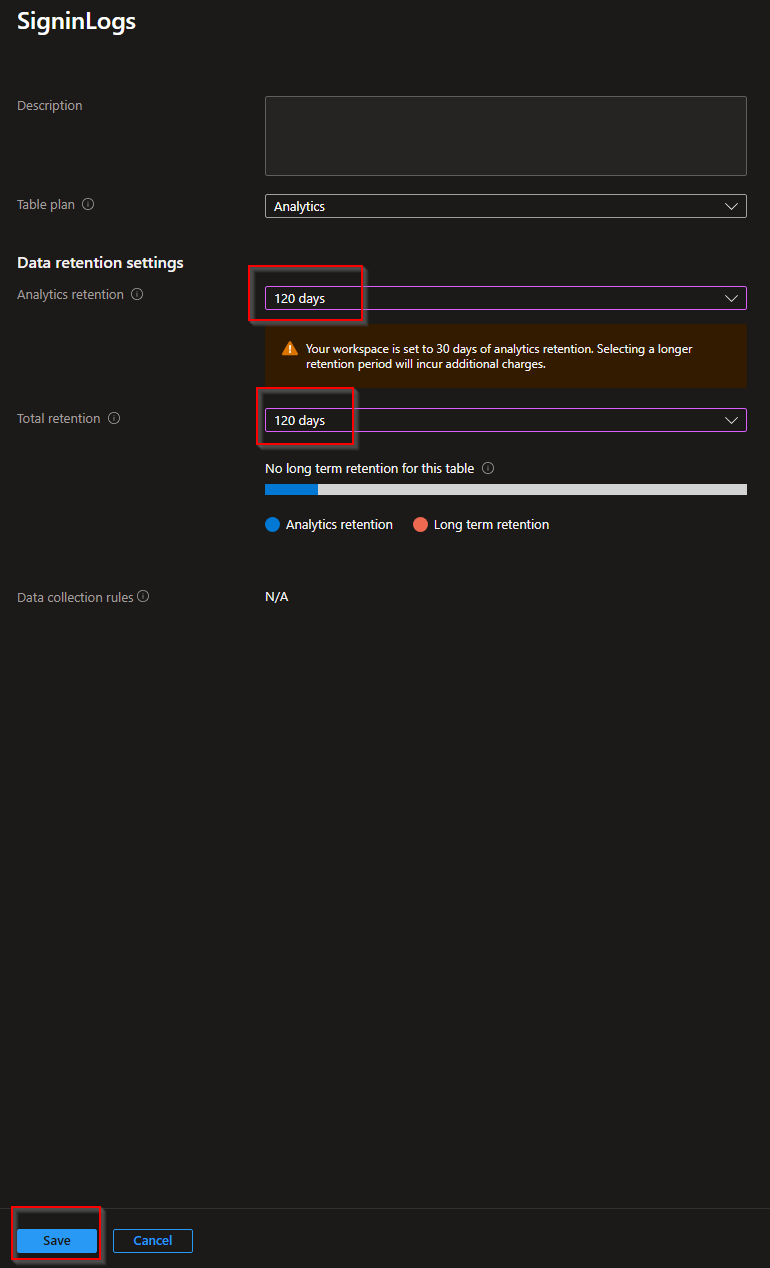
Select Manage table and set the retention you want to have configured for your Sign-In logs. For this blog I set the retention to 120 days. For the whole 120 days you are able to use queries with fast responds.
I recommend applying the same approach to the other logs that we have transferred to the Log Analytics Workspace.
3. Costs Insights
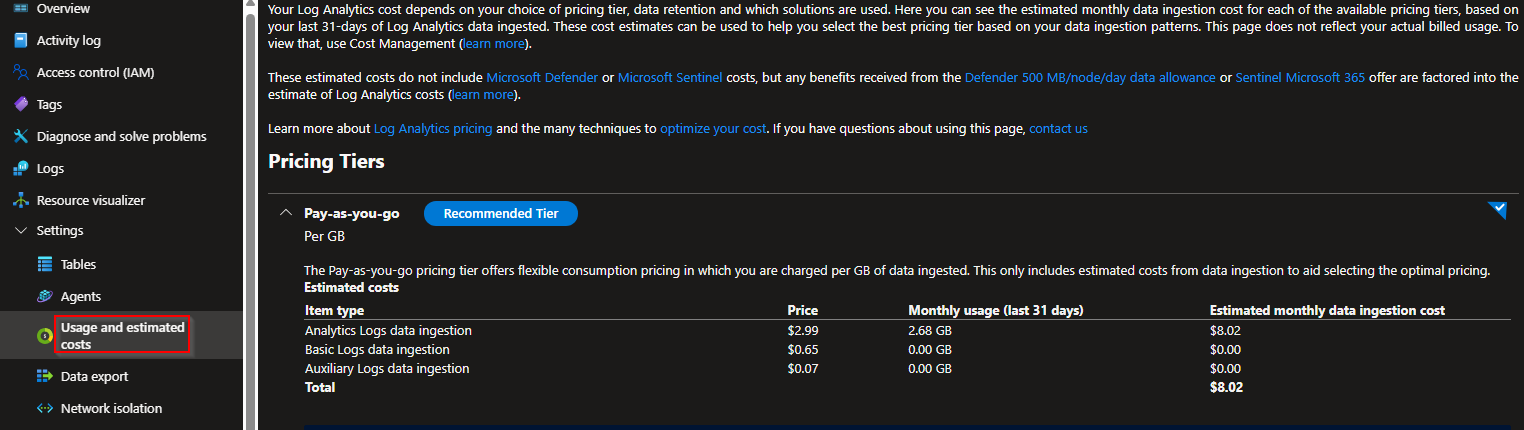
From the "Usage and estimated costs" menu you will be able to see your estimated costs for your logs. Usage will be charged by GB.
4. Practical Kusto Query Language (KQL) Examples
To use KQL queries go to "Logs" and select your table (for example Sign-In Logs). Hereby some examples queries you could run!
Failed Sign-In Attempts by IP Address
SigninLogs
| where ResultType != 0
| summarize FailedAttempts = count() by IPAddress, Location, UserPrincipalName
| sort by FailedAttempts desc
Sign-Ins from Unusual Locations
SigninLogs
| summarize Locations = make_set(Location) by UserPrincipalName
| where array_length(Locations) > 3