[Security: Entra ID] Conditional Access Token Protection (Device Bound Token)

In this blogpost we're going to talk about Conditional Access Token Protection. What is CA Token Protection, what are the requirements and how do I configure this?
1. What is Token Protection?
Token Protection attempts to reduce token replay attacks. In order to do this Microsoft only accepts device bound or token binding sign-in tokens. Device token binding means that when a user logs in this token will stick to their managed device and cannot be transferred to a unmanaged device (the attacker).
*note: this will not work for shared devices. You always need to ensure you have a primary user on the device.
2. Requirements for Conditional Access Token Protection
To be able to use Token Protection you will need to have the following:
License:
- Microsoft Entra ID P1 (a few months back this was only for P2)
Devices:
- Windows 10 or newer (Entra (hybrid)joined or Entra registered
- Windows Server 2019 or newer. Remark that your server needs to be Entra joined
- Preview for MacOS, iOS
- OneDrive sync client version 22.217 or +
- Teams native client version 1.6.00.1331 or +
- Power BI desktop version 2.117.841.0 (May 2023) or +
- Exchange PowerShell module version 3.7.0 or +
- Microsoft Graph PowerShell version 2.0.0 or + with EnableLoginByWAM option
- Visual Studio 2022 or newer when using the 'Windows authentication broker' Sign-in option
- Windows App version 2.0.379.0 or +
2.1 Supported Resources
The following resources are supported for Token Protection. Some features are not (yet) available as you may notice from this list. For example Token Protections supports client applications but not (yet) browser based applications:
Office 365 Exchange Online
Office 365 SharePoint Online
Microsoft Teams Services
Azure Virtual Desktop
Windows 365
3. How To Create A Token Protection Policy
The first thing we want to do is browse to the Entra Admin Center:
Go to the Entra admin center (entra.microsoft.com)
Browse to Entra ID -> Protection -> Conditional Access -> Select Policies
Next select New Policy:
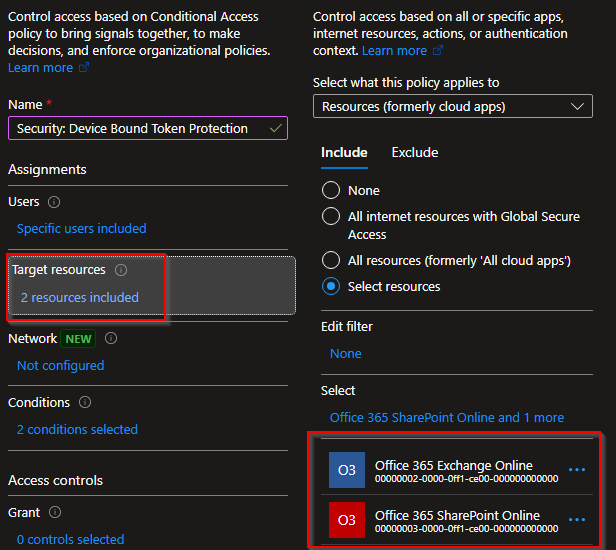
From the new policy screen we are going to name the policy (for example Security: Device Bound Token Protection). From here configure the following options:
Users & Groups:
Select the users or groups you want to include in this policy. I recommend starting with a small set of users.
*note: the users you select need to have devices that are Entra (hybrid)joined or Entra registered.
Target Resources
Office 365 Exchange Online
Office 365 SharePoint Online
*note: if your are using Windows 365, AVD or Windows Cloud login you should also add these.
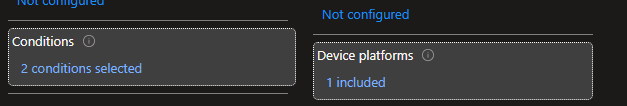
Conditions
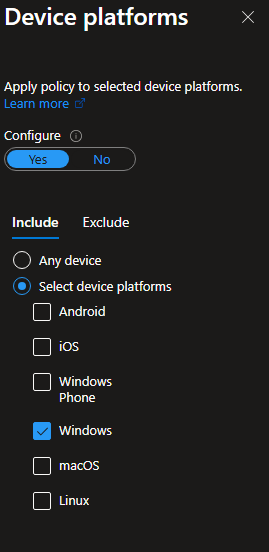
Device Platforms -> Configure -> Yes -> Select Device Platforms -> Windows
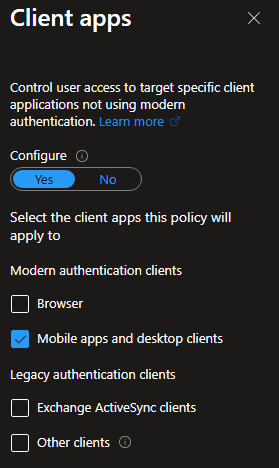
Client Apps -> Configure -> Yes -> Modern Authentication Clients -> Mobile apps and desktop clients
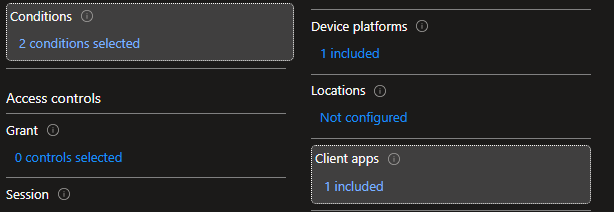
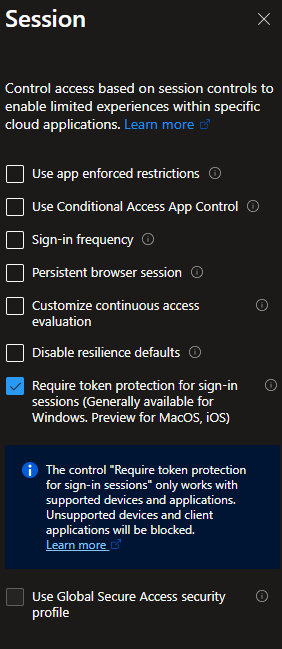
Session
Require token protection for sign-in sessions (Generally available for Windows. Preview for MacOS, iOS)
4. Great! How Can I See If This Works?
Now that we've configured a new CA policy we are ready to test it out! If your user has a device that is Entra (hybrid) joined of registered they won't see any difference.
From a Admin perspective we can check if the policy is working / the token has a device bound token. To check if your policy is working we go to our Entra Sign in logs:
Go to the Entra admin center (entra.microsoft.com)
Browse to Entra ID -> Users -> Select Sign-in logs
From the Sign-in logs search for the user that is member of the Token Protection policy.
*note: to quick search add a (search)filter for example "Username" or search for your application "Teams, Microsoft Outlook"
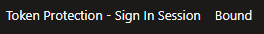
Now that we have found our user, select for example "Microsoft Outlook" and seach for "Token Protection - Sign In Session". You will find this under "Basic Info". If your policy is working you will see Bound:
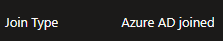
If we look closer we should also see what type of device is used for this authentication. In my demo you will see Azure (Entra) ID joined. You will find this info under "Device Info":
From the conditional access tab select your CA policy. From here you will see your CA policy beieng enforced on your device:

4.1 What About Unmanaged Devices?
From a unmanaged device your connection to Outlook or Teams will be different as you will not be able to login and use those desktop applications. Instead, you will see the following:
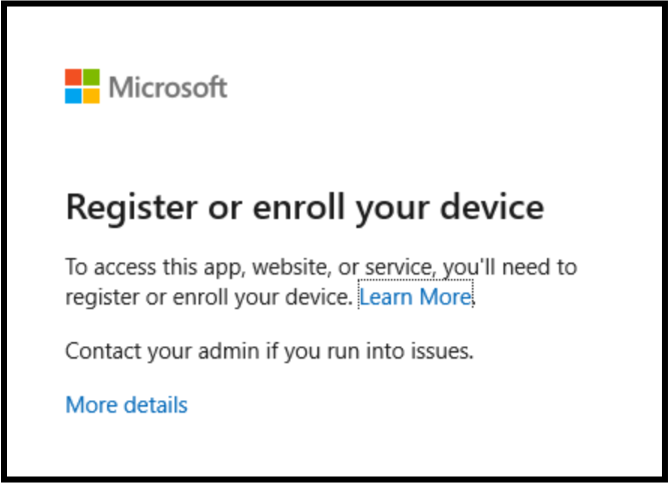
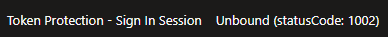
Also in our sign-in logs we see that the token is Unbound with statuscode 1002 which means "The request is unbound due to the lack of MS Entra ID device state".
*Note: you will get the same statuscode/unbound when you are using your browser instead of a client application. This is because Browser apps are not (yet) supported.
5. Wrap-Up
Token Protection is a great feature for your environment. I do strongly recommend not only start using Token Protection but also have configured Phishing Resistant MFA (FIDO key, Passkey). With only Token Protection in place you can still be affected by token replay if you are using browser apps (cookies hash).
Nevertheless I recommend you start using Token Protection as this is a great way to make sure your token is secured when using Client Apps!